From ransomware attacks to cybersecurity threats, hackers have only become craftier. They have moved away from the trend of linear data breaches, making it more difficult to predict their next moves.
Even a simple type of attack can cost precious time and money. More severe data breaches can cripple entire companies. Preventing any type of cyberattack from happening is crucial.
In general, cyberattacks fall into two categories: cyber breaches to retrieve personal data and ransom attacks that demand money from victims. Let’s take a quick look at the effect of each data breach.

How Much Does It Really Cost?
Research shows that the average extortion payment has been projected to increase to $6,000 in 2021. Even worse, projected costs of downtime in the US could increase from $274,000 to $380,000.
The cost is not just monetary, however. Although financial extortion is generally the main aim of hackers, breaches also cause network down time and data loss, as files are sometimes not just stolen but also corrupted or deleted.
Additionally, because intruders copy previously successful attacks, they can target the victims repeatedly with the same campaign, extending the torment and increasing the cost further.
Keep Your Small Business Safe!
We have more than twenty years of experience working with financial firms, so you can be assured that we’ll take care of your every need.

Cyber Intrusion #1: Biggest Social Media (Re)Leak
April 2021
What happened? – In 2019, the personal information of around 533 million Facebook users was leaked. This included phone, locations, bios, birthdate, and in some cases, email addresses.
On the 3rd of April 2021, Alon Gal, Chief Technology Officer at Hudson Rock – a cybercrime intelligence firm – discovered a new data leak.
A Facebook spokesperson in a statement to Axios said “We found and fixed this issue in August 2019.” Facebook, however, does not have much power to limit the spread of information online.
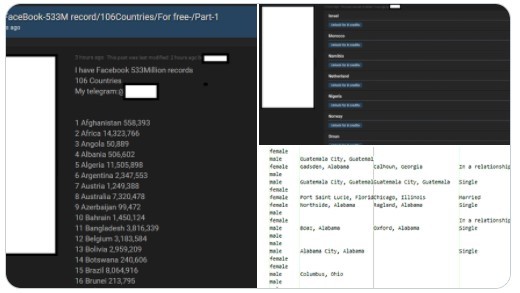
Who was impacted? – Facebook user accounts from 106 countries were exposed. This includes around 32 million in the US, 11 million in the UK, and 6 million in India.
What was the intent? – The people behind these types of leaks usually aim to sell the stolen data to marketers. The buyers then use the data to create targeted adverts.
According to Gal, the cybercriminals could be “taking advantage of the data to perform social engineering attacks [or] hacking attempts.”
Was it successful? – Because the information was successfully leaked to the public, the breach succeeded.
How can you protect yourself? – Eventually, much of the information you share online will probably become public. Facebook should notify victims to watch out for scams and fraud. Because you cannot rely on this, protect yourself from social engineering.
Most people would be suspicious of an email claiming they have won $1 million, but may fall for one from a ‘colleague’ asking for some documents or files.
Train employees to double check the source of all communication.
If your employees suspect their information has been leaked, engage with the professionals to keep all anti-virus software up to date.
Cyber Intrusion #2: Death by Cyberattack? University Hospital Düsseldorf
September 2020
What happened? – Recent cyberattacks on hospitals, especially during the Covid-19 pandemic, have created an urgency that criminals rely on to ensure payments of ransoms.
This was the case at the University Hospital of Düsseldorf when a ransomware invasion caused thirty servers and essential systems to crash.
As emergency patients were turned away, a woman in critical condition died. She was sent to a hospital thirty-two miles away and died as a result of treatment delays.
Although data breaches are known to have severe monetary consequences, this is the first loss of life-related to them.
Some experts state that the seventy-eight-year-old patient would have died regardless of the delay. But as posed by Markus Hartmann at Cologne’s public prosecutor’s office, how long until lack of access to medical care due to a cyber breach directly causes a death? “Where the patient is suffering from a slightly less severe condition, the attack could certainly be a decisive factor,” he says.
Who was impacted? – The most obvious result was the death of a human and the effect on her family and friends.
At the hospital, hundreds of appointments were canceled and the facility halved its treatment capacity.
What was the intent? – Extortion.
Was it successful? – Some reports suggested the campaign was targeting the affiliated Heinrich Heine University and not the hospital. The criminals eventually presented the encryption key when they realized they had affected the hospital.
How can you protect yourself? – This is a case where one data breach affected numerous servers.
To protect your organization, especially in the case of connect systems, create a layered defense system. This will ensure that even if an attacker breaks through one layer, they cannot access the protected data.
Cyber Intrusion #3: Dangerous Water Treatment Hack
February 2021
What happened? – In Oldsmar, Florida, events usually played out only in Hollywood movies came to life.
The city’s water treatment system was breached. In what could have been a deadly cyberattack, an unknown individual gained access to the system’s control systems. They then increased the levels of sodium hydroxide to deadly levels. The chemical used in drain cleaners was increased from 100 parts per million to 11,100 parts per million!
The hacker gained access through TeamViewer, a commonly used application that gives workers access to all team members’ computers. Usually used for remote troubleshooting and access to internal networks, it was the perfect path for the breach.
All the computers at the treatment system used the same password, and with outdated OS, it was fairly easy for the hacker to monitor and adjust chemical levels.
Luckily, the employee with the hacked desktop noticed the intrusion and re-adjusted the chemicals to a safe level before anyone was physically affected.

Who was impacted? – There was no direct effect on any person, but this could have become one of the most serious breaches if it had been left undetected.
What was the intent? – According to the Cybersecurity and Infrastructure Security Agency, critical infrastructure is an “attractive target for foreign powers attempting to do harm to US interests or retaliate for perceived US aggression.”
Although not confirmed, this has been touted as one of the motives behind the trespass.
Was it successful? – Thankfully, no.
How can you protect yourself? – Security experts say the breach could have been avoided if workers had secured their passwords and access rights.
Make sure all your systems and servers are up-to-date and occasionally choose new, strong passwords, without repeating the same one across any two accounts.
Cyber Intrusion #4: Marriot Hotel Chain “Counter-Intelligence” Hacks
September 2018

What happened? – In 2016, Marriott acquired Starwood hotels and its IT systems – as well as unwelcome encryption.
Hackers had used a remote access trojan (RAT), along with a tool called MimiKatz that is used to discover username/password combos, to get into the systems. With these tools, they were able to bypass cybersecurity features and access customer data.
Who was impacted? – Marriott reported that 500 million guest records were hacked. Access to sensitive personal information, including credit card and passport details, made customers open to identity theft.
The hotel group was fined £18.4 million by the Information Commissioner’s Office in the UK.
What was the intent? – Apart from identity theft, reports in the US said the cyberattack was part of a Chinese intelligence-gathering mission backed by government agencies.
Was it successful? – This breach lasted so long and was so successful that it probably serves as a case study for future attackers.
How can you protect yourself? – The threat of a breach in hotels’ systems is especially high because of the many points of entry. Guests can usually book via a booking engine that connects to the central reservations system.
The data is then logged into the PMS and internal CRM or even revenue management systems.
It’s easy to see why hotels are easy targets and need extremely high levels of cybersecurity.
If you are in the hotel industry or have a business that is constantly collecting data, make sure to use a quality cloud property management system (PMS).
Cyber Intrusion #5: CPI’s Almost Cataclysmic Attack
January 2020

What happened? -Communication & Power Industries, or CPI, is a major electronic manufacturer for the communications and defense markets. The company makes military components used for radar, electronic warfare technology, and missile seekers by the US Department of Defense.
An employee with a domain admin password clicked on a malicious link and triggered a file-encrypting malware.
CPI confirmed the attack, with spokesperson Amanda Mogin saying, “We are working with a third-party forensic investigation firm to investigate the incident.”
Who was impacted? – Thousands of computers in the CPI office were infected. Even scarier, the one-site backups were also at risk.
Numerous files of sensitive information from the Defense Advanced Research Projects Agency (DARPA) were also encrypted.
What was the intent? – Extortion.
Was it successful? – This was a case in which there was no time to waste. The company quickly paid the ransom of $500,000 and received the decryption key. However, it struggled to get all of its devices operational again after the fact.
How can you protect yourself? – The moral of this story? Upgrade your operating systems frequently.
Do not use outdated software, as was the case of CPI, who was using Microsoft Windows XP, the updates for which had stopped in 2014. Not a good idea, especially if you work for the government!
Cyber Intrusion #6: Widespread Demant Breach
September 2019
What happened? – In the costliest intrusion of 2019, Danish hearing aid manufacturer Demant’s IT infrastructure was almost completely crippled. Their worldwide systems were disrupted, affecting customers’ orders and services.
Who was impacted? – The total cost, as confirmed by the firm, was “an estimated $80 million to $95 million, even though the company held a cyber insurance policy. Without that policy, the bill would have been $14.6 million higher.” The incident also impacted their international partners.
For more than two weeks afterward, Demant was not able to supply products, process orders, or service users across its network.
What was the intent? – Although reported as ransomware by Danish news, there has been no official report by the organization.
Was it successful? – While the payment of an extortion fee was not confirmed, the overall loss showed the huge negative impact the breach had on the business.
How can you protect yourself? – The best way to protect your company from the same fate as Demant is to have tailor-made protection and support from the experts.
Cyber Intrusion #7: Cognizant “Maze” Attack
April 2020
What happened? – A New Jersey-based IT services provider called Cognizant was the unfortunate victim of the biggest US ransomware attack in 2020.
Maze was one of the most frightening types of malware. It not only blocked access to user accounts if victims refused to pay extortion fees, but the criminals behind Maze also posted user data on a public website.
They also provided downloads and even links to Facebook or Twitter.
Luckily, the Maze ransomware group announced in November 2020 that they had closed down their ransomware operation.
In a press release, the Maze team said, “Maze Team Project is announcing it is officially closed. All the links to ou[r] project, using of our brand, our work methods should be considered a scam.”
Who was impacted? – Cognizant workers were unable to enter the organization’s internal network. No one could log in to their official email address, and the encrypted servers and files were only recovered after three weeks.
What was the intent? – Extortion.
Was it successful? – Apart from halting all communication between employees, Cognizant said they expected to lose between $50 – $70 million.
This was a result of lost revenue as well as the cost of recovery and mitigation efforts.
How can you protect yourself? – So, is there anything you can do to protect your business against a similar breach?
Engaging professional cybersecurity services is your best option. They are skilled at fixing software vulnerabilities.
This includes patching and updating your OS, security software, and internet browsers, which can keep your business safe from similar cybercriminals
Cyber Intrusion #8: The Cyberattack That Makes You “WannaCry”
May 2017
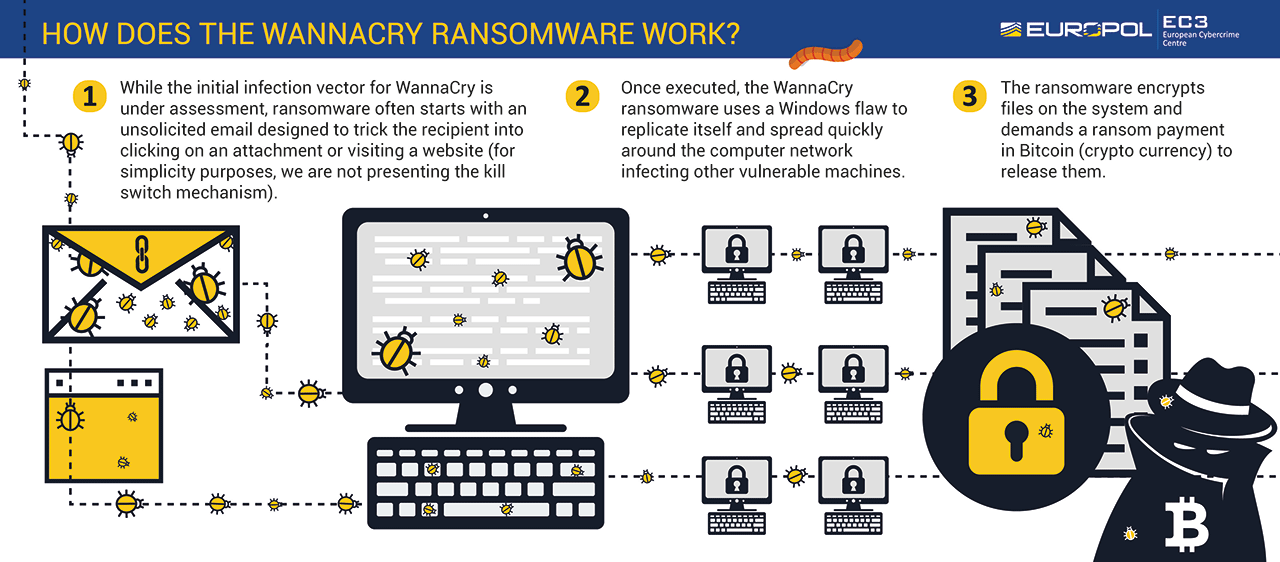
What happened? – In 2017, one of the biggest worldwide cyberattacks spread across more than 150 countries in just a few days.
WannaCry is a crypto-ransomware that encrypts data, limits access, and then demands payment, usually in Bitcoins.
Also known as WannaCrypr, WRrypt, and WCRY, it’s thought to have been part of a highly coordinated cyberattack. The malware was spreading like a worm, affecting a flaw in the Windows SMB protocol. According to Europol, such invitations usually started with an unsolicited email that prompts people to click on an attachment or link.
Once activated, WannaCry spread through numerous networks, affecting machines with vulnerabilities.
It was developed after classified National Security Agency hacking tools were stolen and published online.
Who was impacted? – Hours after the attack was launched, hospitals across the UK had to shut down their appointment systems.
Images on Twitter and Facebook showed National Health Service computers with demands for payments of $300 worth of Bitcoin. “Ooops, your files have been encrypted!” said the cheeky message.
This was followed by an explanation that the only way to recover files was with the hackers’ decryption services.
This ransomware affected more than twenty NHS hospitals in the health industry, including ambulances. It also affected government systems, railway networks, and private companies.
What was the intent? – Extortion. The group gave explicit instructions to pay one of three bitcoin addresses.
Was it successful? – The malware was stopped after Marcus Hutchins, a malware reverse-engineer, found WannaCry’s killswitch. The infections stopped, but there were Twitter reports by an Avast researcher of 36,000 devices already having been infected in Russia, Ukraine, and Taiwan.
Kaspersky said that globally, the number hit around 230,000 computers, and extortion payments totaled $386,905.
How can you protect yourself? – The breach affected only Microsoft systems, like those in the healthcare industry. Those systems have likely now all been updated, but that doesn’t mean that a similar infection couldn’t break out on a different system.
Be careful of opening any unfamiliar link, especially one in an attachment. If it asks you to enable macros or unlock, do not open the link. Create and check data backups often.
Understanding Cybersecurity Breaches
Apart from ransomware, some other common types of security threats can also have personal and financial consequences. This applies to both individuals’ devices and companies’ servers.
According to Bruce Schneier, dubbed a ‘security guru’ by the Economist, “Data is the pollution problem of the information age, and protecting privacy is the environmental challenge.”
Government organizations are also starting to understand the challenge. The National Cybersecurity Center has recognized that cybersecurity is more important than ever. They recently launched a program to educate state leaders about cyber threats.
Research by Verizon in 2020 found that breaches were a result of six major reasons, mainly:
- Hacking – 45%
- Human error – 22%
- Social attacks – 22%
- Malware – 17%
- Misuse by authorized users – 8%
- Physical actions to devices – 4%
Phishing has been ranked the most common type of attack, featuring in news reports across the US, and globally. First used during the mid-90s, phishing was behind 22% of data breaches in 2020.

Usually sent by email, a phishing cyberattack hides malicious content, often in a link.
Savvy hackers disguise email URLs from which they send fake company news or communication. Some ask for users’ information, and by clicking on a malware link, people can inadvertently give access to their user passwords.
The Covid-19 pandemic has also provided more opportunities for criminals to use phishing to compromise business emails.
There are ways to protect yourself from these types of security breaches, but to put the risks into perspective, take a look at some of the most dramatic and catastrophic cyberattacks.
Ransomware and Its Negative Impact
Statistics show that many companies face an imminent ransom threat – but most do not know it. New variants are constantly popping up, having increased by up to 46% in 2019.
The FBI has also stated that “ransomware attacks are becoming more targeted, sophisticated, and costly…” Attacks are so common that a business is targeted every 14 seconds.
Cyber extortion is not an easy battle to win, but the best way is to have the proper knowledge. It is key to understanding how hacking happens and who it targets.
Even more importantly, anyone who works with tech devices or a source code must know the real cost of data breaches.
Who Is Most at Risk?
Companies across the world reported ransom attacks within the last year, and even countries with the most sophisticated security technologies are at risk.
These include big American, Chinese, and Middle East-based companies that have fallen victim.
The numbers are simply shocking, with between 50% to 88% of companies in these countries reporting a ransomware attack.
In North America, government agencies and bodies are the most attacked organizations. They reported 15.4% of all attacks in the US, followed by manufacturing and construction at 13.9% and 13.2%, respectively.
Keep Your Business Protected
According to Verizon, two-thirds of companies that had experienced a security breach said the experience had a major negative impact on the business.
As our CEO Raffi Jamgotchian’s book On Thin Ice explains, you could easily fall prey to cyberattacks if your business isn’t well-prepared, even if you are aware of the danger.
Get your copy of the book that offers experience from thirty-one experts. With rave reviews, it is a great starting step to learning the most effective cybersecurity solutions and securing your organization.
Additional reading: “The Shadow Pandemic: Ransomware’s Present and Future Dangers for Corporations”. https://www.toptal.com/insights/innovation/fighting-ransomware-attacks.
Keep Your Small Business Safe!
We have more than twenty years of experience working with financial firms, so you can be assured that we’ll take care of your every need.

