You’ll always need IT protection
Because cyber criminals never stop.
That’s why we embed cybersecurity best practices into our Fully and Co-Managed IT Services plans.
After 23+ years in the cybersecurity and IT Services industry, I know how hard it can be, at times, to grasp the full scope of cyber threats detection and prevention.
That’s why I wrote a chapter on security frameworks for the book, On Thin Ice. It’s basically the culmination of everything that I walk my clients through to keep them safe and sound.
“A sure sign of a mature or maturing organization is the adoption and use of a security framework. Raffi provides a succinct intro to a few such frameworks and explains the benefits of choosing one or more for your business. Along the way he shows the multitude of issues involved and summarizes them within the security pyramid which makes keeping a high-level view of what’s involved easily possible.”
Sevag Ajemian, Founder, Globanet Consulting
It’s vital that all business owners and executives understand cybersecurity services and frameworks so that they can invest their dollars wisely. This is where our “Pyramid of Security” comes into play.
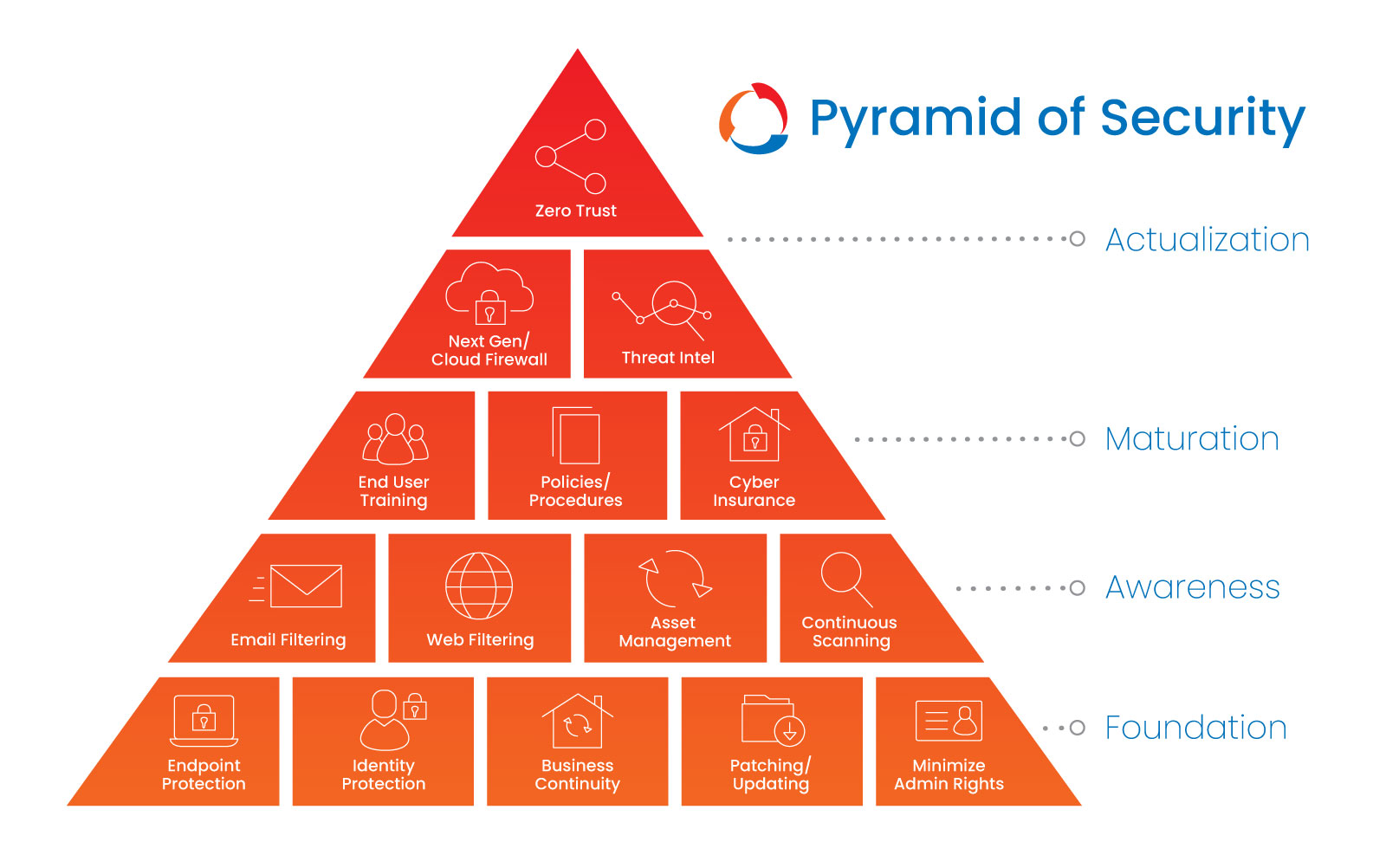
This pyramid is designed to guide you through the 15 minimum requirements of any security program.
Actualization
Zero Trust Networking
When it comes to networking, “zero trust,” says it all: don’t automatically trust anything inside or outside of your network “perimeter.” Create and follow policies and approval criteria for access to your IT systems. This means that users, devices and networks can gain entry only after being verified. Also, every device operates as a network segment with posture-based policies. In addition, only applications on the approved allow-list can run on said devices.

Next-Gen / Cloud Firewall
Since basic routers (like the one from your internet provider) lack the ability to log activities for future review and correlation, against known and emerging aggressors, you’ll need a next-generation firewall or a unified threat management system. These two solutions provide advanced filtering and network segmentation options, which prevent certain devices from communication with other devices (think phones, cameras, servers, etc.). In addition, Secure Access Service Edge (SASE) are baked into cloud platforms to ensure secure and fast cloud transformation. Also, it’s vital to centrally host your firm’s firewall activities across a cloud infrastructure and provide secure access to both cloud and private networks and applications. All of this is important to gain visibility into your company’s network activity especially with workers increasingly operating remotely.

Threat Intelligence
The end game for threat intelligence is to identify who, how and why a bad actor is trying to gain access to your IT systems. It also, helps provide more details on indicators of compromise (IOCs), which is data pulled from log entries that shows signs of malicious activities, and assists in identifying actionable events, ways to counteract threats. It’s important that you also do your part in staying current on all threats targeting your industry. Look for both public and paid resources and sign up for intelligence feeds. Better yet, consult your IT Service partner to find out what threat intelligence sources they use.
Maturation

End User Cybersecurity Awareness Training
Though it’s unfortunate, most breaches are due to phishing and human error. This makes your employees and contractors your first line of defense against cyber threats. So, be sure to educate them regularly on the latest cybersecurity threats, how to avoid and report them if they make a mistake. Then, test their knowledge via physical penetration tests and simulated phishing attacks. Be sure to use failure as an opportunity to re-educate rather than shame them.

Policies / Procedures
Policies not only define your company’s standards for using systems and data, they also set the rules on how IT administrators, managers and end users should interact with them. When creating policies be sure to at least include the baseline recommendations and the reason for the policy. Explain the “why.” After the policies are written, be sure to build out the procedures that define what processes your team should follow.

Cyber Insurance
Though cybersecurity insurance is for all businesses, if you’re in a highly regulated industry, say financial services or healthcare, you should definitely invest in it. Cybersecurity is typically not covered by general liability policies but it highly valuable for helping protect businesses again computer related crimes and losses. Especially, because it can assist in covering remediation and regulatory fines. However, be aware that cyber insurance comes with its own compliance requirements in order to receive benefits in the event of a breach, ransomware or other cyberattack. Be sure to read and comply with the fine print.
Awareness

Email Filtering
Email is the most popular site for cybersecurity attacks and breaches. In fact, it’s most hacker’s top choice. To prevent all sorts of spam, viruses and potential phishing, be sure to filter both inbound and outbound email. Also, encrypt all sensitive data sent via email to prevent loss or leakage of sensitive information. Be prepared to identify impersonation email and to keep out malware that typically hides in attachments and links. Lastly, be sure to log your message traffic in case there is a breach. This will be invaluable to your investigation and containment efforts. in the case a breach happens.

Web Filtering
As fun as it sounds, it’s important to filter internet browsing in your office. This serves a myriad of purposes. It filters out unwanted websites that might be knowingly or unknowingly hosting malware via their ads and email links. It also reduces the potential for data exfiltration and work distractions while helping ensure regulatory compliance. Do this by using the next-gen firewall we discussed earlier. If you have team members working remotely or traveling, you may need an addition app to provide this function.

Asset Management
Catalog and keep track of all your hardware, applications, virtual servers and data to best protect it. Forgotten, unsupported assets and disorganized data are a bad actor’s pipe dream. This is because assets and data that are tracked and managed typically fail to get timely updates making them vulnerable to exploitation or prolonged downtime. In addition, have a plan in place for updating and replacing equipment.

Continuous Scanning
It’s all in the name. A large part of cybersecurity is continuously scanning your networks, devices and data for vulnerabilities caused by poor configurations, patch management failures or malicious activities. You want to catch and address these before cyber criminals do. In addition, continuous scanning also discovers unknown assets and may be required by some compliancy programs.
Foundation

Endpoint Protection
Endpoints are devices used to interact with your data (think computers and mobile phones). In general, you’ll need more than traditional anti-virus software to protect them. The best approach includes detecting and preventing any problems using digital forensics, creating and enforcing endpoint policies and identifying and remediating against footholds. It’s also important to identify which apps are allowed to run and then, whitelisting them. However, when it comes to cell phones a more robust protection plan is in order. Afterall, we use them constantly to connect, communicate, entertain and order take out. This means they have easy access to all kinds of data from the super sensitive to the mundane. The best practice here is to use a mobile device management system to ensure security and compliance. However, some employees might frown on having a corporate app on their personal phone. If this is the case, consider investing in company-owned devices for your team. Having this level of security will pay off in the long run.

Identity Protection
As identities are becoming more and more the norm for accessing resources it’s important to guard them fiercely. Sometimes, it’s the only thing keeping your data from falling into the wrong hands. When we talk about identity protection, typically it’s at the level of passwords. Everyone has a love/hate relationship with their passwords. They need to not only be strong but random and unique, which makes them hard to remember. But you need to remember them, which typically makes them less strong. A conundrum, right? The best way around this is to sign up for a password manager so that you can find them when you need them. In addition to creating strong, unique passwords, use multi-factor authentication, a software authenticator, a token or biometrics whenever possible.

Business Continuity
All kinds of disasters can happen from the natural to human made error or those of malicious intent. It only takes one disaster to cause a business to fail so having continuity or disaster recovery plan is non-negotiable. Business continuity plans need to include remediations for both local and remote impact, backups and recovery steps. They should also be disconnected from production systems to prevent malware spread. When it comes to backups, the ideal scenario would be to have multiple data backups including one offsite copy (or cloud copy) for the least 30 days, though 90 days is best. Keep multiple backups of your data, including at least one copy offsite. Plus, make sure to continually test your backups to ensure you can restore your data in case you ever need to. Lastly, be sure to run annual full recovery tests and to automate them.

Patching / Updating
Operating systems, software, web browsers, firmware and drivers have flaws. Unfortunately, these flaws can easily be exploited by bad actions. This makes patching and updates critical to keeping your IT systems and infrastructure secure. The best time to install critical patches and security updates is as soon as they’re released but at least within the first 7 days for actively exploited vulnerabilities and 30 days for patches and updates that are not addressing cybersecurity issues.

Minimize Administrative Rights
Be judicious in which employees get access to which data, devices and applications. Basically, avoid granting administrative rights to all users. First, not every user needs admin rights and second, it’ll be difficult to protect your IT infrastructure and systems effectively the more admin users you have. By minimizing administrative rights, you’re able to reduce the attack surface on devices, prevent software from being installed in areas that could cause critical damage and make it impossible for most users to disable security features. Also, consider adding other layers of defense such as allow-listing software.
Please know that these 15 minimum security program solutions are not the be all, end all of your cybersecurity needs. These are merely the start.
If you’re interested in learning more about security frameworks, please contact me via the form below for a free copy of “What is a Security Framework?”
“Raffi Jamgotchian’s chapter 31, What is a Security Framework, in the book, On Thin Ice is a must read. He lucidly defines them, describing the most common ones. Raffi then goes on to demystify the “pyramid of security” in easy-to-understand steps, so you have a comprehension and comfort with the terminology and importance of security. In twenty minutes, I went from knowing very little to a working knowledge, which every business executive should have.”
Parag Saxena, CEO, Vedanta Capital Management