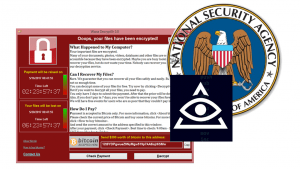
WannaCry, a relatively new addition to the ransomware scene, wreaked havoc on networks worldwide, starting with UK’s National Health Service (NHS) on Friday May 12th and by Monday had reached over 300,000 computers in 150 countries according to a report on npr.org.
What is Ransomware?
We’ve discussed it before, but Ransomware is particular type of malicious software or malware that will take your data hostage in return for a monetary ransom. In the early days, this was requested by sending Visa prepaid and iTunes gift cards. With the advent of digital currencies such as Bitcoin, it has grown, to the point that ransomware incidents will actually drive up the value of bitcoin during these events. In the case of modern ransomware, and WannaCry is no exception, it works to encrypt or scramble your files with a unique password which will be unlocked with the paid ransom.
Why is the NSA involved in this?
Some tools used by the National Security Agency was exposed by a group calling itself the Shadow Brokers. They claimed to have stolen these tools from an internal NSA hacking group called the Equation Group. In April a bunch of these tools were exposed publicly including several that work against Microsoft products. Microsoft had patched these vulnerabilities in March (speculation is that the NSA informed Microsoft of these vulnerabilities after their tools were compromised).
The Global Spreading
This malware spread globally because it not only had to rely on people clicking on a malicious link in email (which is what is alleged here) but would move throughout the network hitting unpatched machines (computers that haven’t gotten the latest fixes from Microsoft), In addition computers that were exposed to the Internet that hadn’t been patched yet were also infected without any person having to click on anything. In addition to encrypting your files, this variant was also dropping a remote access trojan (RAT) so they can come back and access your computer again in the future.
Fortunately a group of security researches at MalwareTech.com discovered a kill switch, which is a trigger to stop the malware from further spreading, and it has died down. However, as predicted, there are new variants without the kill switch that are starting to be seen in the wild.
Steps We Have Taken for all our Managed Clients
We are making sure that all systems are properly patched with the latest from Microsoft. Typically we will update several test computers at each company the first week an update is released and the remainder the following week. But due to the nature of this outbreak, we are ensuring that all systems are up to the May patch levels (even though this was fixed in March).
We have also taken steps to disable the services that are vulnerable. In this case, they are not needed for most computing.
Our Webroot Antivirus system has the proper updates in place to prevent an infection.
Backups are being monitored as normally to ensure that if anything does through other defenses, that we can quickly recover from a ransom situation for data being backed up.
We’re here to help you. We’re taking all the necessary steps to protect our clients. No process is 100% so there are always some good practices you should take:
Be wary of attachments and links sent to you from people you don’t know or even do know.
Any attachment that asks you to click on a link or enable macros to unlock, don’t do it
When in doubt, ask us.
Steps You Can Take
Make sure your personal computers are up to date, search for Windows Update on your computer at home (Mac’s are not affected by this, but you should make sure they are up to date too.
Make sure you back up your personal files to a place that does some sort or versioning so that if you’re infected and the infected files are backed up they don’t overwrite your backup. Most good cloud backup providers will do this.
Don’t open up emails from people you don’t know, especially if they have links or attachments. If you do open an attachment and it asks you to enable Macros or click on a link to “unlock” the file, DON’T DO IT. if you’re not sure, ask us and we can assess.
Did I mention to check your backups, maybe do it twice, once to a local drive and once offsite at least once a day.
If you do think you were infected (i.e. suddenly your filenames start changing and you can’t open them) pull the plug on your computer.