How do you know you are protected from cyber-attacks? Do you understand the basic tactics employed by hackers to gather your information? Why do small businesses need cybersecurity services? We created this guide to help users avoid mistakes that could make them a victim of an attack.
Triada Networks is a lead provider in IT security solutions for hedge funds.
It provides a basic understanding of what phishing and spear-phishing attacks look like and common ways to protect yourself from them.
You might be surprised at how hackers try to gain access to your information.
What is Phishing?

Phishing is a cyber-attack usually sent in the form of an email, text message, or a popup web form. Hackers “cast a wide net” when sending out phishing emails to try to bait as many users as possible.
The most common type of phishing attack comes in the form of a spoofed email, which will entice the user to click on a link to reset their password, log in to an account, or share personal information.
Phishing emails are generally not targeted to specific individuals but rather sent out to large groups of people. Phishing emails often spoof known brands such as Microsoft, Office 365, or Apple. The hacker sends an email with a fake link to a landing page that features a trusted brand.
The emails will often contain phrases like “Reset Your Password” or “Your Password Has Expired.”
If you enter your credentials into the popup, the hacker will gain access to sensitive information stored within that account.
What is Spear Phishing?
Spear phishing is targeted at specific individuals. A spear-phishing attack is more refined than a traditional phishing attack. This type of attack uses social engineering, social media, and personal information to target people and business employees to click on malware or a phishing email link.
Spear phishing emails are generally believable because the cybercriminal used accurate personal details to entice a user to take quick action. Sometimes they will direct a user to a specific account site where they must complete steps, or their account will be closed.
They are often used to target a company or organization by using an employee’s login information to get access to the business network or sensitive company data.
Sometimes spear-phishing attacks are difficult for email security programs to catch because they seem like legitimate business emails.
Key Differences: Phishing vs Spear Phishing
Phishing emails are generally sent to a large number of people. They are intended to catch as many users as possible with their wide net approach.
On the other hand, spear phishing emails are used to specifically target one individual and convince them to give up their data.
A spear-phishing email tends to be more specific and accurate than regular phishing emails since the cyber attackers conduct research on the individual before sending the email. Phishing emails typically contain poorly written instructions with a simple clickable link to redirect many users to a popup window.
Warning Signs of a Spear Phishing Attack
Phishing emails are generally sent to a large number of people. They are intended to catch as many users as possible with their wide net approach.
On the other hand, spear phishing emails are used to specifically target one individual and convince them to give up their data.
A spear-phishing email tends to be more specific and accurate than regular phishing emails since the cyber attackers conduct research on the individual before sending the email. Phishing emails typically contain poorly written instructions with a simple clickable link to redirect many users to a popup window.
Check the Sender’s Email
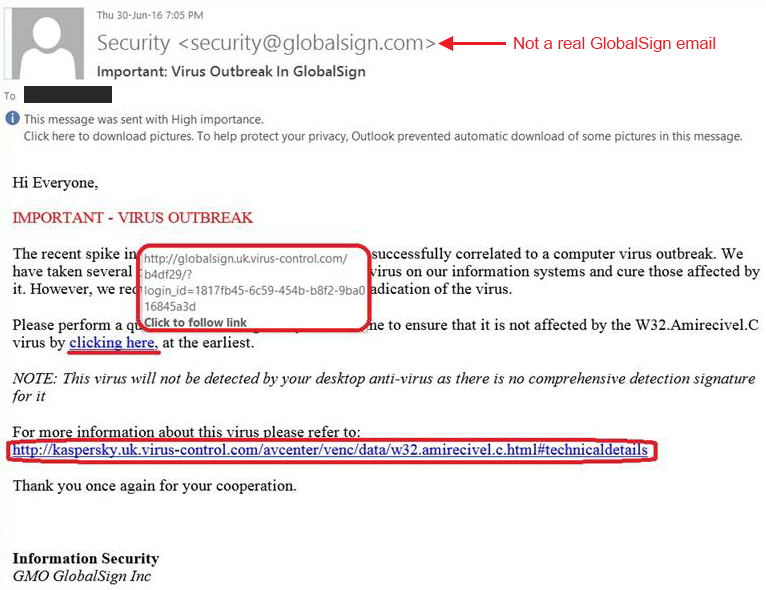
The first thing to look for in spear-phishing attacks is the “from” field of the email. You should check to see if the sender’s email address matches the name of the sender. If it is spelled incorrectly or has many random letters and numbers after it, then it is likely a scam.
Always check the spelling of the sender’s email address. For example, many malicious emails might have a slight difference in spelling, such as “apple.co” or “googl.com.” This is an early warning sign of phishing attacks.
Do Not Click!
The number one rule of thumb is, do not click on anything until you verify the source of the email. You can hover your cursor over a link to see where it is really going to send you before clicking.
Greeting
Remember to check the greeting of the email for clues. If the sender addresses you by “sir” or “madam” instead of your name, then it is likely a malicious email.
Grammar and Spelling
Most phishing attack emails are poorly written since some of them are written by malware bots. If the email you received is generally free of spelling errors and everything else checks out, then it could be legitimate.
Tone
What is the overall tone of the email? If the sender is using a sense of urgency that is unusual, then it might be a fake email. One key tactic used by an attacker is they want you to do something immediately that you normally wouldn’t do. It could be something like changing your password, updating contact information, or closing an account.
Tips to Protect Yourself From Phishing Attacks
Social Engineering
How much information are you sharing online? To protect yourself from future spear phishing cyber attacks, you should take a look at your online profiles. You should monitor the personal and sensitive information you post online.
Check your privacy settings to ensure that only a limited number of people you trust can view the data.
Phishing Protection Software
For your protection, we recommend investing in an anti-phishing attack software to scan emails that come through your inbox. Phishing protection software will scan all of your files to ensure that they don’t contain malware.
You should always keep other software up to date with the latest security patches.
Password Security
Check your password security on all of your accounts. A secure password should contain random letters, numbers, and characters.
We understand that it may be easier to have the same password across all of your accounts, but we recommend using different passwords for each account.
If all of your passwords are the same, an attacker will effectively have access to every account that contains sensitive information.
Company Training
Since many spear-phishing scams are intended to affect business employees, we recommend providing training to employees who work in your office and have access to sensitive client data. IT security and training might include an example of a phishing scam and how to tell the difference between legitimate and scam emails.
You might want to train employees in your organization on the dangers of social engineering. If your company is targeted with a phishing attack, it is important that employees know what to do and who to report to.
Employee awareness will greatly reduce the chances of your company data being compromised.
Takeaway
Did you know that in the first half of 2020 there were about 146,994 reported phishing attacks? The internet can be a dangerous place, especially for your personalized accounts and information. Many people fall victim to phishing attacks every day, but that doesn’t have to be you.
We hope this guide has armed you with the knowledge to keep your accounts secure and unharmed from malicious cyber attacks. The more you know about them, the easier it will be to protect yourself.
