It’s a sad reality that ransomware has become so common and that any unprotected company could risk falling victim.
Ransomware attacks are a type of malware that blocks access to a computer or a network’s operating systems when activated. Malware is so common that over 18 million websites are infected with malware each week.
The software holds the data hostage, then extorts a ransom payment. When the ransom demanded is paid, the business will receive a decryption key to regain access to their systems and data.
Lately, the use of ransomware Trojans has become more numerous, complicated, and costly. Trojans contribute to 51.45% of malicious software, and 7 out of 10 cyber threats were ransomware.
The FBI states that there has been a 37% increase in ransomware incidents between 2018 and 2019.
In addition, there has also been a 147% increase in how much ransomware costs businesses during the same period, including ransomware.
Managed Service Providers (MSPs) report ransomware to be the most common threat that their small and medium business clients (SMBs) face.
A survey of over 1,000 MSPs found that 60% reported that their SMB clients have faced more ransomware attacks than ever before – especially with the onset of COVID-19.
Since the onset of the pandemic, unscrupulous cybercriminals have been posing as workers for the Center for Disease Control (CDC) or the World Health Organization (WHO).
The FBI estimates that more than 100,000 computers are infected by ransomware every day.
These numbers are quite stunning and are set to continue rising during 2021.
If you are reading this, you have possibly come across the phrase “ransomware attack,” but what are the real stats?
When we look specifically at ransomware, it is expected that an organization will fall victim every 11 seconds in 2021.
Here we look at the most recent ransomware statistics, trends, and data, and a few examples to help protect yourself from ransomware attacks.
Recent Ransomware Attacks in 2021
The average ransom per incident has almost doubled from $4,300 in 2018 to $8,100 in 2020 and total ransomware costs will be up to $20 billion in 2021 in the US.
Ransomware costs caused by downtimes have also increased by more than 600% since 2018. This represents an $8,500 loss per hour as a result of downtime.
Ransomware Attack #1: Dairy Farm’s Emails Leaked
When was the incident? January 2021
What happened? On average, the ransom requested does not exceed a few hundred thousand dollars.
The request during a ransomware attack to Dairy Farm, however, was for $30 million. The huge Pan-Asian company operates more than 10,000 outlets with over 200,000 employees across Asia.
The company operates multiple groceries, home furnishing, and restaurant brands, including Ikea, 7-Eleven, and Wellcome, among others.
A well-known IT blog was contacted by a member of the REvil ransomware group who said they had encrypted Dairy Farm’s computer network on the 14th of January.
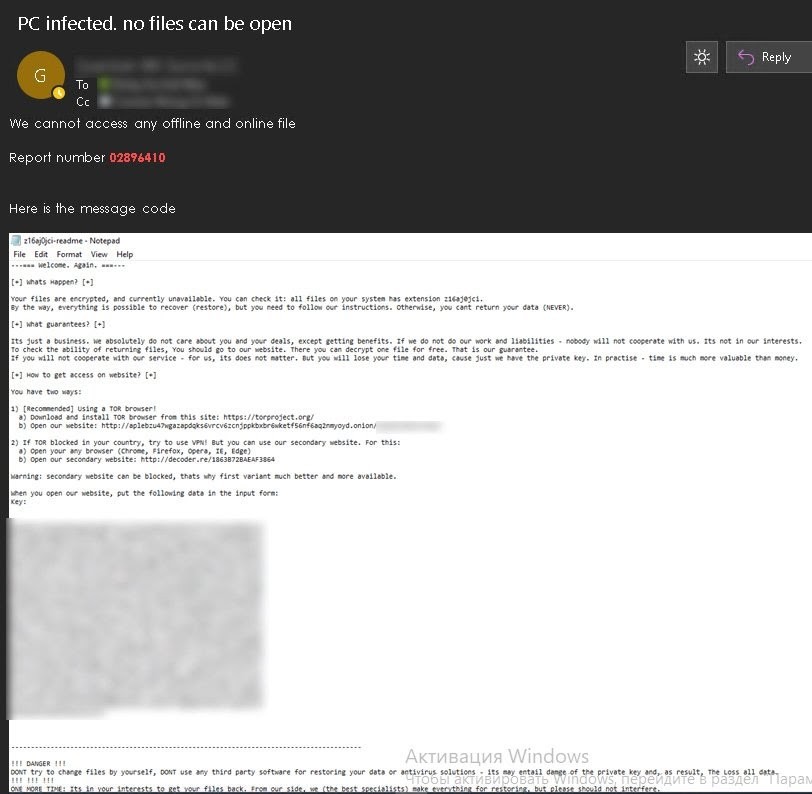
Dairy Farm confirmed that they had been the victim of a cyberattack. They said that less than 2% of their networks had been affected.
The affected networks were quickly taken offline and isolated. They also recruited a security specialist to improve their security measures and monitoring systems.
Proof shows that the attack was still ongoing nine days after discovery, however.
The attackers had full control of the company’s email systems, as well as their internal networks, threatening to release company information to the public.
Ransomware Attack #2: Acer’s Largest Ransom Ever
When was the incident? March 2021
What happened? The well-known electronics and computer maker Acer faced a ransomware attack that requested a whopping $50 million, making it the largest ransom demand to date.
The Taiwanese company has around 7,000 employees and earned $7.8 billion in 2019. The REvil gang announced that they had breached Acer, sharing some allegedly stolen files on their website.
The documents included financial statements, bank balances, and bank communications. When asked for details, an Acer representative said, “There is an ongoing investigation and for the sake of security, we are unable to comment on details.”
The hackers offered a 20% discount if the ransom was paid by a set date, and they would delete the stolen files and offer a decryptor and a vulnerability report.
They also threatened that the price would be doubled if the deadline was passed.
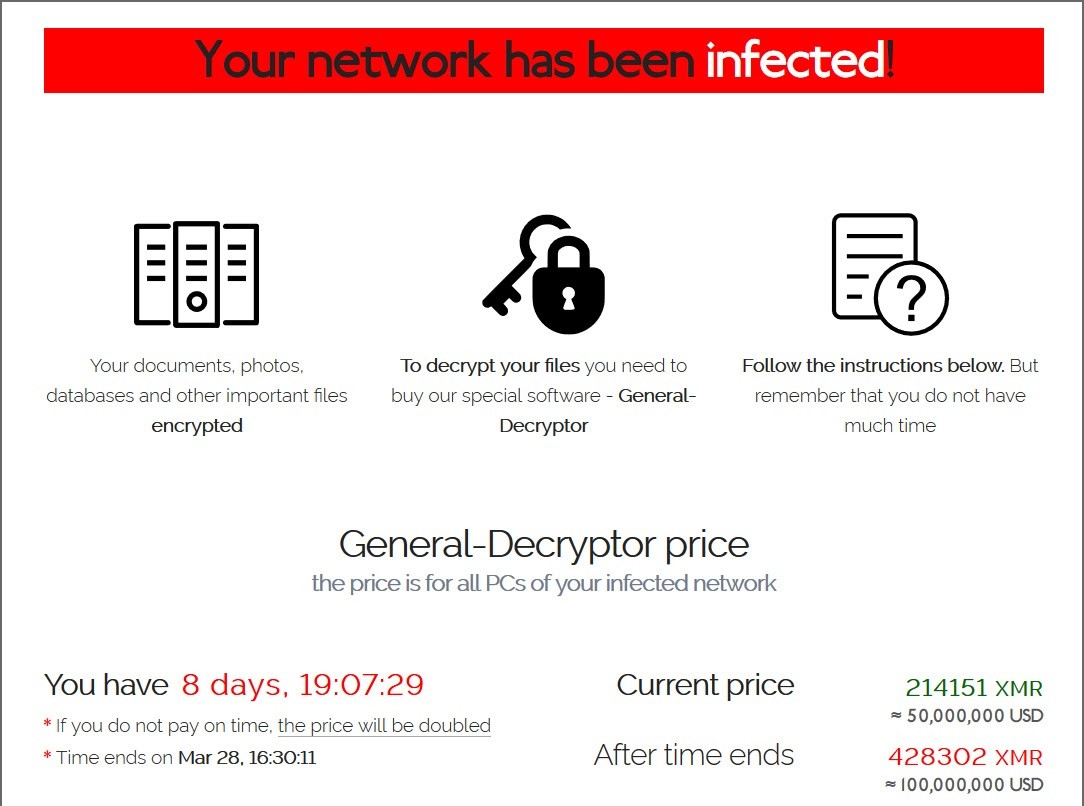
Acer did not deny or acknowledge the attack, but they did confirm that “companies like us are constantly under attack.”
They stated that they had reported the recent abnormal activity to law enforcement and data protection authorities.
The Acer spokesperson said the company could not provide further details due to the nature of the investigation.
Ransomware Attack #3: Spain’s Public Service Agency Crippled

When was the incident? March 2021
What happened? In one of the latest Ryuk ransomware attacks, Spain’s Public Payments Agency – Servicio Público de Empleo Estatal (SEPE) – was crippled, and the systems were made unavailable.
The bad actors behind Ryuk are suspected to have used one of their new ransomware threats that feature “worm-like” capabilities.
The SEPE website displays a message saying they have suffered a security incident and the organization is working to contain and isolate the attack.
The Ryuk ransomware has resulted in all payments to citizens, companies, and other beneficiaries have been halted. This hurts people who need to demand employment funds, as this service will be delayed.
The ransomware was reused in over 710 state offices, telematics systems, and some laptops of remote workers.
It is believed that the ransomware attack infiltrated the organization through an unpatched networking device that allowed the hackers to gain access to one of Spain’s most important public sector organizations.
Ransomware Attack #4: Attacking COVID-19 Vaccination Program
When was the incident? May 2021
What happened? Unfortunately, even as hospitals struggle to roll out COVID-19 vaccines, there are bad actors set on slowing down progress.
Healthcare providers have been under constant cyberattacks, and a major one in Germany even resulted in the death of a patient.
The latest ransomware attack in the healthcare industry happened in mid-May, affecting Ireland’s Health Service Executive (HSE). The whole system was forced to shut down all of its IT systems, both locally and nationally.
Bitcoin was demanded by the perpetrators of the ransomware attack, but officials stated they will not pay the ransom. The online registration was also offline for some time but was quickly restored online.
The attack affected hospitals around the country, and staff was unable to access patient records and test results or send emails. Some appointments had to be canceled, but HSE worked quickly to assess the situation.
How Much Does Ransomware Cost Businesses in 2021?
The average ransom per incident has almost doubled from $4,300 in 2018 to $8,100 in 2020 and total ransomware costs will be up to $20 billion in 2021 in the US.
Ransomware costs caused by downtimes have also increased by more than 600% since 2018. This represents an $8,500 loss per hour as a result of downtime.
The reason that ransomware attacks cost so much is the time it takes for organizations – especially smaller businesses – to regain their data.
Ransomware-induced downtime is often more costly than the ransom demand.
Research shows that “Downtime costs are typically 5 to 10 times the actual ransom amount and are measured in lost productivity (slack labor and lost revenue opportunities).”
In 2021, it is predicted that cybercrime-related damage, including ransom attacks, could reach up to $6 trillion annually.
Keep Your Small Business Safe!
We have more than twenty years of experience working with financial firms, so you can be assured that we’ll take care of your every need.

Who Is Most at Risk of a Ransomware Attack?
Ransomware attacks occur indiscriminately and affect all types of businesses.
From educational institutions, healthcare providers, and small businesses, unless proper security measures are in place, no one is safe.
Even cybersecurity professionals are unsure about how to repel ransomware attacks, especially with new ransomware variants.
Some of the organizations that are most at risk include:
- Government Institutions
Up to date, nearly 60 million Americans have been victims of identity theft that affect their government-issued documents and accounts. In 2020 alone, the U.S Federal State Commission received 1.4 million reports of identity theft – a 50% increase from 2019.
During 2019, ransomware attacks affected 103 federal, state, and municipal governments and agencies making attacks against state and local governments the top stories of the year.
- Small Businesses
SME’s account for 43% of all cyberattacks, as they sometimes cannot invest in cybersecurity. Additionally, 20% of ransomware victims are small to midsize businesses.
Only 29% of small businesses have had experience with any type of ransomware, making them unlikely to be prepared for a ransomware threat.
- Financial Institutions
90% of all financial institutions reported having experienced a ransomware infection within the past year, and attacks on small banks and credit unions are increasing.
As of March 2020, 52% of cyberattacks were in the financial service sector, and more than 70% were caused by the Kryptik trojan software.
- Healthcare Sector
The average cost of a cyberattack in healthcare organizations was about $20.8 billion that was spent on paying the ransom, rebuilding lost data, and paying for lawsuits.
IT professionals in healthcare organizations don’t believe that healthcare providers are ready to deal with ransomware attacks and encryptions in the National Healthcare System (NHS) had a number of negative results that could have been life-threatening.
These included treatment without access to patient records, clinical history, and prescription details. Ambulances were also rerouted and appointment records unavailable.
Healthcare organizations are extremely prone to attacks because of the critical nature of their work. They cannot afford to lose their data, so hackers expect them to quickly pay the ransom demand.
They are also extremely vulnerable because Personal Health Information (PHI) can sell for hundreds of dollars and can be resold to many different people. Health systems are also checked in terms of compliance – not security levels.
Vulnerabilities on connected devices such as printers and medical devices can also work as a doorway through which malware can infiltrate hospital software.
- Educational Institutions
Out of 17 surveyed industries, the education industry is ranked as the least prepared in terms of cybersecurity, and 61% of 7.7 million security breaches in 2019 affected educational organizations.
Because of the rise in remote learning and teaching, schools and universities have become more vulnerable to cyberattacks. Studies have shown that there were more than 300 cybersecurity-related incidents at schools in 2019, and over 1,000 spear-phishing attacks have been recorded in the education sector.
According to the FBI, schools and universities are the most popular target for ransomware attacks. Schools are an easy target because 50% of students and educators do not have any cybersecurity training.
Even with the onset of virtual learning, 60% of teachers did not receive additional security training and get minimal tech support.
- Social networking site Twitter experienced a significant breach that attacked 130 high-profile accounts. Victims included past US presidents, Elon Musk, and others. Hackers also managed to steal about $121,000 in Bitcoin across a total of around three hundred cyber transactions.
- Several million records were exposed through data breaches aimed at other social networking sites, including Facebook, Instagram, Tik Tok, and Youtube.
- International hotel chain Marriott reported a major cyber breach in 2020. The data breach impacted over 5.2 million hotel guests, exposing their private information, including sensitive data such as credit card information.
- Carnival Corporation, the largest cruise ship operator in the world, experienced a ransomware attack that resulted in a massive data breach in August 2020. The cyberattack exposed confidential information relating to the business’s employees and guests. Security services reported that in addition to exposing the records, the hackers encrypted a vital portion of the company’s IT infrastructure.
- Adult live streaming website CAM4 was hacked in 2020, with hackers exposing over 10 billion records. A research team discovered that the system had been breached in March, with the breach ongoing for over a month.
- Two hundred and one records were exposed by a breach in the Google Cloud server.
Should Ransomware Victims Pay the Ransom?
As per many government regulations that no one should ever give in to blackmail or ransoms, the same applies to ransomware threats.
Law enforcement agencies, including the Cybersecurity and Infrastructure Security Agency (CISA) and the FBI, advise against making ransom payments.
This could embolden owners of the ransomware to attack more IT systems and also encourage other hackers to use similar methods.
If the data breach results in encrypted data, making a ransom payment does not guarantee that your files will be recovered. Additionally, businesses that paid the ransom could be funding criminals, including organized crime networks and terror organizations.
These government bodies urge ransomware victims to let them deal with any reported incidents.
In 2020, the US Treasury signaled that facilitating ransomware payments may be illegal. The move came after a rise in “consultants” who help businesses pay cybercriminals.
Before this, companies could choose whether to pay ransom demands, but these independent decisions are coming under governmental oversight.
According to Alon Gal, one of the world’s foremost cybersecurity experts, said, “It is a game changer…We are going to see a much tougher handling of these incidents.”
Cybersecurity firms that help businesses make ransomware payments might have to register as a part of the money services industry in response to calls for new reporting requirements in the industry.
Regardless, many ransomware attack victims have paid the ransom, as they would otherwise have lost revenue and stolen data.
A survey of 600 businesses shows that they paid the ransom demands at higher rates compared to consumers. These ransomware stats show that 20% of successful attacks were paid an average ransom payment amount of $40,000. 25% paid between $20,000 and $40,000.
As mentioned, one of the major costs involved with ransom is ransomware downtime.
Loss of sensitive files, like financial and sales records, and lost revenue can have a long-term effect on the business and may even result in temporary or permanent closures.
Few businesses expose the fact that they are ransomware victims to avoid public humiliation. They also fear the loss of customer confidence and business goodwill.
Many others keep the ransomware attacks secret, usually paying by Bitcoin.
Data shows that 29% of large businesses’ executives are willing to pay more than $50,000 to recover their financial records back. 24% would pay the same amount for their sales records.
Cybersecurity statistics are shocking due to the growing number of threats and their massive impact on the whole world. Although the cybersecurity market has developed in leaps and bounds, with the pandemic opening up new malicious opportunities for cybercriminals, these hackers’ new schemes will likely only get harder to handle.
As security experts report, companies are now realizing how vital it is to hire professionals to stem the tide of cyberattacks upon their livelihood. With the evolving creation of sophisticated cybersecurity hacks, business owners should consider complementing their own IT teams with professional cybersecurity firms that offer AI-backed technology.
If you want the best protection for your business’s systems, consider our company. We offer amazing tech solutions and top-notch cybersecurity; contact us for a free consultation!
Protect Yourself From Ransomware Today!
As we can see that ransomware attacks are getting more intricate, as well as more expensive, you cannot afford to not invest in complete ransomware protection.
It is worth your time and money to keep your antivirus software up-to-date, as well as constantly be on the hunt for malicious software in your systems.
By engaging with expert security analysts, they can fish out cyber threats hiding in your network and prevent any threats from slipping past antivirus software.
If you do have a breach, Triada Networks is essentially the 911 of cybersecurity.
By performing security risk assessments, system monitoring, and audits, we can keep your personal data, as well as your business, safe.
We are available to offer the best advice about your cybersecurity and IT needs. Schedule a free consultation today.
Keep Your Small Business Safe!
We have more than twenty years of experience working with financial firms, so you can be assured that we’ll take care of your every need.

